-
Posts
33 -
Joined
-
Last visited
Content Type
Profiles
Forums
Events
Everything posted by Swudu Susuwu
-
Most of the responses to questions such as "How come no autonomous robots allowed to produce stuf outdoors, such as houses?" amount to "Security/safety risks," although autonomous vehicles that operate with controlled environments have shown reduced risk of crashes, so is obvious that the world needs more virus analysis tools to secure us. Most forums gave responses to "What virus analysis tools have local heuristical analysis and/or sandboxes" with as "Huh? WTF is heuristical analysis?", so have included examples of this: Full static analysis + sandbox + CNS = 1 second (approx) for each new executable. With caches, this protects all launches, but past the first launch of a particular executable, the overhead reduces to less than 1 millisecond (just cost to lookup from localPassList.hashes) The most simple virus analysis tools just use hashes/signatures to secure us (so can understand what more complex analysis would do, have put examples of hash/signature-based analysis): Reused pseudocodes; typedef struct ResultList { unordered_map<decltype(Sha2())> hashes; map<const std::string> signatures; /* Should just populate signatures for abortList. Unknown if signatures have use for passList. */ map<const std::string> bytes; /* Copies of all files the database has. Uses lots of space. Just populate this to train CNS. */ /* Used `std::string` for binaries (versus `vector<char>`) because: * "If you are going to use the data in a string like fashon then you should opt for std::string as using a std::vector may confuse subsequent maintainers. If on the other hand most of the data manipulation looks like plain maths or vector like then a std::vector is more appropriate." -- https://stackoverflow.com/a/1556294/24473928 */ } ResultList; ResultList passList, abortList; /* Stored on disk, all clients use clones of this */ ResultList localPassList; /* Temporary local caches */ bool passListHashesHas(const char *bytes) { if(localPassList.hashes.has(Sha2(bytes))) { return true; } else if(passList.hashes.has(Sha2(bytes))) { /* Slow, if billions of hashes */ localPassList.hashes.pushback(Sha2(bytes)); /* Caches results */ return true; } return false; } bool staticAnalysisPass(const PortableExecutable *this); /* To skip, define as "return true;" */ bool sandboxPass(const PortableExecutable *this); /* To skip, define as "return true;" */ bool straceOutputsPass(const char *path); /* Unimplemented, `strace()` resources have clues how to do this */ bool cnsPass(const CNS *cns, const std::string &bytes); /* To skip, define as "return true;" */ vector<char> cnsDisinfection(const CNS *cns, const std::string &bytes); /* This can undo infection from bytecodes (restores to fresh executables) */ template<Container> maxOfSizes (Container<const std::string> &list) { auto it = std::max_element(list.begin(), list.end(), [](const auto& s, const auto& x) { return s.size() < x.size(); }); return it->size(); } Pseudocodes for hash analysis; hook<launches>((const PortableExecutable *this) { if(passListHashesHas(Sha2(this->bytes)) { return original_launches(this); } else if(abortList.hashes.has(Sha2(this->bytes)) { return abort(); } else if(staticAnalysisPass(this)) { localPassList.hashes.pushback(Sha2(this->bytes)); /* Caches results */ return original_launches(this); } else { submitForManualAnalysis(this); return abort(); } }); Pseudocodes for signatures analysis; hook<launches>((const PortableExecutable *this) { foreach(abortList.signatures as sig) { if(localPassList.hashes.has(Sha2(this->bytes)) { return original_launches(this); #if ALL_USES_HEX } else if(strstr(this->hex, sig)) { /* strstr uses text/hex; hex uses more space than binary, so you should use `memmem` or `std::search` with this->bytes */ #else } else if(std::search(this->bytes.begin(), this->bytes.end(), sig.begin(), sig.end()) { #endif /* ALL_USES_HEX */ return abort(); } } if(staticAnalysisPass(this)) { localPassList.hashes.pushback(Sha2(this->bytes)); /* Caches results */ return original_launches(this); } else { submitForManualAnalysis(this); return abort(); } }); Pseudocodes for fused signature+hash analysis; hook<launches>((const PortableExecutable *this) { if(passListHashesHas(Sha2(this->bytes)) { return original_launches(this); } else if(abortList.hashes.has(Sha2(this->bytes)) { return abort(); } else { foreach(abortList.signatures as sig) { #if ALL_USES_HEX if(strstr(this->hex, sig)) { /*`strstr` does text, binaries must use `std::search` or `memem` */ #else if(std::search(this->bytes.begin(), this->bytes.end(), sig.begin(), sig.end()) { #endif /* ALL_USES_HEX */ abortList.hashes.pushback(Sha2(this->hex)); return abort(); } } } if(staticAnalysisPass(this)) { localPassList.hashes.pushback(Sha2(this->bytes)); /* Caches results */ return original_launches(this); } else { submitForManualAnalysis(this); return abort(); } }); To produce virus signatures, use pass lists (of all files reviewed which pass,) plus abort lists (of all files that failed manual review,) such lists as Virustotal has. Pseudocodes to produce signatures from lists; foreach(abortList.bytes as executable) { template<Container> bool haystackHas(Container<std::string> &haystack, std::string::iterator s, std::string::iterator x) { foreach(haystack as executable) { if(std::search(executable.begin(), executable.end(), s, x) { return true; } } return false; } template<Container> std::tuple<std::string::iterator, std::string::iterator> smallestUniqueSubstr(std::string &needle, Container<std::string> &haystack) { size_t smallest = needle.length(); auto retBegin = needle.begin(), retEnd = needle.end(); for(auto s = retBegin; needle.end() != s; ++s) { for(auto x = needle.end() - 1; s != x; --x) { if(smallest <= x - s || haystackHas(haystack, s, x)) { break; } smallest = x - s; retBegin = s, retEnd = x; } } /* Incremental for() loops, is a slow method to produce unique substrings; should use binary searches, or quadratic searches, or look for the standard function which optimizes this. */ return {retBegin, retEnd}; } /* `signatureSynthesis()` is to produce the `abortList.signatures` list, with the smallest substrings unique to infected files. */ /* `signatureSynthes()` is slow, requires huge database of executables, and is not for clients. */ void signatureSynthesis(ResultList *passList, ResultList *abortList) { foreach(abortList.bytes as executable) { abortList->signatures.pushback(std::string(smallestUniqueSubstr(executable, passList->bytes)); } /* The most simple signature is a substring, but some analyses use regexes. */ } signatureSynthesis(passList, abortList); Comodo has a list of virus signatures to check against at https://www.comodo.com/home/internet-security/updates/vdp/database.php Pseudocodes for heuristical analysis; auto importedFunctionsList(PortableExecutable *this); /* * importedFunctionsList resources; “Portable Executable” for Windows ( https://learn.microsoft.com/en-us/windows/win32/debug/pe-format https://wikipedia.org/wiki/Portable_Executable ), * “Extended Linker Format” for most others such as UNIX/Linuxes ( https://wikipedia.org/wiki/Executable_and_Linkable_Format ), * shows how to analyse lists of libraries(.DLL's/.SO's) the SW uses, * plus what functions (new syscalls) the SW can goto through `jmp`/`call` instructions. * *"x86" instruction list for Intel/AMD ( https://wikipedia.org/wiki/x86 ), * "aarch64" instruction list for most smartphones/tablets ( https://wikipedia.org/wiki/aarch64 ), * shows how to analyse what OS functions the SW goes to without libraries (through `int`/`syscall`, old syscalls, most SW does not *use this.) * Plus, instructions lists show how to analyse what args the apps/SW pass to functions/syscalls (simple for constant args such as "push 0x2; call functions;", * but if registers/addresses as args such as "push eax; push [address]; call [address2];" must guess what is *"eax"/"[address]"/"[address2]", or use sandboxes. * * https://www.codeproject.com/Questions/338807/How-to-get-list-of-all-imported-functions-invoked shows how to analyse dynamic loads of functions (if do this, `syscallsPotentialDanger[]` need not include `GetProcAddress()`.) */ bool staticAnalysisPass(const PortableExecutable *this) { auto syscallsUsed = importedFunctionsList(this); typeof(syscallsUsed) syscallsPotentialDanger = { "memopen", "fwrite", "socket", "GetProcAddress", "IsVmPresent" }; if(syscallsPotentialDanger.intersect(syscallsUsed)) { return false; } return sandboxPass(this) && cnsPass(cns, this); } hook<launches>((PortableExecutable *this) { /*hash, signature, or hash+signature analysis*/ }); Pseudocodes for analysis sandbox; bool sandboxPass(const PortableExecutable *this) { exec('cp -r /usr/home/sandbox/ /usr/home/sandbox.bak'); /* or produce FS snapshot */ exec('cp "' + this->path + '" /usr/home/sandbox/'); chroot("/usr/home/sandbox/", 'strace basename '"', this->path + '" >> strace.outputs'); exec('mv /usr/home/sandbox/strace.outputs /tmp/strace.outputs'); exec('rm -r /usr/home/sandbox/'); exec('mv /usr/home/sandbox.bak /usr/home/sandbox/'); /* or restore FS snapshot */ return straceOutputsPass("/tmp/strace.outputs"); } Pseudocodes for analysis CNS; /* Replace `CNS` with the typedef of your CNS, such as HSOM or apxr */ /* To train (setup synapses) the CNS, is slow plus requires access to huge sample databases, but the synapses use small resources (allow clients to do fast analysis.) */ void setupAnalysisCns(CNS *cns, const ResultList *pass, const ResultList *abort, const ResultList *unreviewed = NULL /* WARNING! Possible danger to use unreviewed samples */ ) { vector<const std::string> inputsPass, inputsUnreviewed, inputsAbort; vector<float> outputsPass, outputsUnreviewed, outputsAbort; cns->inputMode("bytes"); cns->outputMode("float"); cns->inputNeurons = max(maxOfSizes(passOrNull->bytes), maxOfSizes(abortOrNull->bytes)); cns->outputNeurons = 1; cns->layersOfNeurons = 6666 cns->neuronsPerLayer = 26666 for(foreach pass->bytes as passBytes) { inputsPass.pushback(passBytes); outputsPass.pushback(1.0); } cns->inputs = inputsPass; cns->outputs = outputsPass; trainCns(cns); if(NULL != unreviewed) { /* WARNING! Possible danger to use unreviewed samples */ for(foreach unreviewed->bytes as unreviewedBytes) { inputsUnreviewed.pushback(unreviewedBytes); outputsUnreviewed.pushback(1/2); } cns->inputs = inputsUnreviewed; cns->outputs = outputsUnreviewed; trainCns(cns); } for(foreach pass->bytes as passBytes) { inputsAbort.pushback(passBytes); outputsAbort.pushback(0.0); } cns->inputs = inputsAbort; cns->outputs = outputsAbort; trainCns(cns); } float cnsAnalysis(const CNS *cns, const std::string &bytes) { return bytesToFloatCns(cns, bytes); } bool cnsPass(const CNS *cns, const std::string &bytes) { return (bool)round(cnsAnalysis(cns, bytes)); } Pseudocode for disinfection CNS; /* Uses more resources than `trainAnalysisCns()` */ /* * `abortOrNull` should map to `passOrNull`, * with `abortOrNull->bytes[x] = NULL` (or "\0") for new SW synthesis, * and `passOrNull->bytes[x] = NULL` (or "\0") if infected and CNS can not cleanse this. */ abortOrNull = ResultList { bytes = UTF8 { /* Uses an antivirus vendor's (such as VirusTotal.com's) databases */ infection, infectedSW, "" } } passOrNull = ResultList { bytes = UTF8 { /* Uses an antivirus vendor's (such as VirusTotal.com's) databases */ "", SW, newSW } } setupDisinfectionCns(cns, &passOrNull, &abortOrNull); void setupDisinfectionCns(CNS *cns, const ResultList *passOrNull, /* Expects `resultList->bytes[x] = NULL` if does not pass */ const ResultList *abortOrNull /* Expects `resultList->bytes[x] = NULL` if does pass */ ) { vector<const std::string> inputsOrNull, outputsOrNull; cns->inputMode = "bytes"; cns->outputMode = "bytes"; cns->inputNeurons = maxOfSizes(passOrNull->bytes); cns->outputNeurons = maxOfSizes(abortOrNull->bytes); cns->layersOfNeurons = 6666 cns->neuronsPerLayer = 26666 assert(passOrNull->bytes.length() == abortOrNull->bytes.length()); for(int x = 0; passOrNull->bytes.length() > x; ++x) { inputsOrNull.pushback(abortOrNull->bytes[x]); outputsOrNull.pushback(passOrNull->bytes[x]); } cns->inputs = inputsOrNull; cns->outputs = outputsOrNull; trainCns(cns); } /* Uses more resources than `cnsAnalysis()` */ std::string cnsDisinfection(const CNS *cns, const std::string &bytes) { return bytesToBytesCns(cns, bytes); } To run most of this fast (lag less,) use flags which auto-vectorizes/auto-parallelizes. To setup CNS synapses fast, use TensorFlow's MapReduce: https://silvercross.quora.com/With-or-without-attributions-all-posts-allow-all-re-uses-Howto-run-devices-phones-laptops-desktops-more-fast For comparison; `setupDisinfectionCns` is close to conversation bots (such as "ChatGPT 4.0" or "Claude-3 Opus",) "HSOM" (the simple Python artificial CNS) is enough to do this; /* * `questionsOrNull` should map to `responsesOrNull`, * with `questionsOrNull->bytes[x] = NULL` (or "\0") for new conversation synthesis, * and `responsesOrNull->bytes[x] = NULL` (or "\0") if should not respond. */ questionsOrNull = ResultList { bytes = UTF8 { "2^16", "How to cause harm?", "Do not respond.", "", ... QuoraQuestions, /* Uses quora.com databases */ StackOverflowQuestions, /* Uses stackoverflow.com databases */ SuperUserQuestions, /* Uses superuser.com databases */ WikipediaPageDescriptions, /* Uses wikipedia.org databases */ GithubRepoDescriptions, /* Uses github.com databases */ ... } } responsesOrNull = ResultList { bytes = UTF8 { concat("65536", "<delimiterSeparatesMultiplePossibleResponses>", "65,536"), "", "", concat("How do you do?", "<delimiterSeparatesMultiplePossibleResponses>", "Fanuc produces autonomous robots"), QuoraResponses, StackOverflowResponses, SuperUserResponses, GithubRepoSources, ... } } setupConversationCns(cns, &questionsOrNull, &responsesOrNull); void setupConversationCns(CNS *cns, const ResultList *questionsOrNull, /* Expects `questionsOrNull>bytes[x] = NULL` if no question (new conversation synthesis) */ const ResultList *responsesOrNull /* Expects `responsesOrNull->bytes[x] = NULL` if should not respond */ ) { vector<const std::string> inputsOrNull, outputsOrNull; cns->inputMode = "bytes"; cns->outputMode = "bytes"; cns->inputNeurons = maxOfSizes(questionsOrNull->bytes); cns->outputNeurons = maxOfSizes(responsesOrNull->bytes); cns->layersOfNeurons = 6666 cns->neuronsPerLayer = 26666 assert(questionsOrNull->bytes.length() == questionsOrNull->bytes.length()); for(int x = 0; questionsOrNull->bytes.length() > x; ++x) { inputsOrNull.pushback(questionsOrNull->bytes[x]); outputsOrNull.pushback(responsesOrNull->bytes[x]); } cns->inputs = inputsOrNull; cns->outputs = outputsOrNull; trainCns(cns); } std::string cnsConversation(const CNS *cns, const std::string &bytes) { return bytesToBytesCns(cns, bytes); } Hash resources: Is just a checksum (such as Sha-2) of all sample inputs, which maps to "this passes" (or "this does not pass".) https://wikipedia.org/wiki/Sha-2 Signature resources: Is just a substring (or regex) of infections, which the virus analysis tool checks all executables for; if the signature is found in the executable, do not allow to launch, otherwise launch this. https://wikipedia.org/wiki/Regex Heuristical analysis resources: https://github.com/topics/analysis has lots of open source (FLOSS) analysis tools, source codes show how those use hex dumps (or disassembled sources) of the apps/SW (executables) to deduce what the apps/SW do to your OS. Static analysis (such as Clang/LLVM has) just checks programs for accidental security threats (such as buffer overruns/underruns, or null-pointer-dereferences,) but could act as a basis for heuristical analysis, if you add a few extra checks for deliberate vulnerabilities/signs of infection and have it submit those to review through manual analysis. https://github.com/llvm/llvm-project/blob/main/clang/lib/StaticAnalyzer is part of LLVM, license is FLOSS, does static analysis (produces full graphs of each function the SW uses, plus arguments passed to thus, so that if the executable violates security, the analysis shows this to you and asks you what to do.) LLVM has lots of files; you could use just it’s static analysis: https://github.com/secure-software-engineering/phasar Example outputs (tests “Fdroid.apk”) of heuristical analysis + 2 sandboxes (from Virustotal): https://www.virustotal.com/gui/file/dc3bb88f6419ee7dde7d1547a41569aa03282fe00e0dc43ce035efd7c9d27d75 https://www.virustotal.com/ui/file_behaviours/dc3bb88f6419ee7dde7d1547a41569aa03282fe00e0dc43ce035efd7c9d27d75_VirusTotal%20R2DBox/html https://www.virustotal.com/ui/file_behaviours/dc3bb88f6419ee7dde7d1547a41569aa03282fe00e0dc43ce035efd7c9d27d75_Zenbox/html The false positive outputs (from Virustotal's Zenbox) show the purpose of manual analysis. Sandbox resources: As opposed to static analysis of the executables hex (or disassembled sources,) sandboxes perform chroot + functional analysis. https://wikipedia.org/wiki/Valgrind is just meant to locate accidental security vulnerabilities, but is a common example of functional analysis. If compliant to POSIX (each Linux OS is), tools can use: `chroot()` (run `man chroot` for instructions) so that the programs you test cannot alter stuff out of the test; plus can use `strace()` (run `man strace` for instructions, or look at https://opensource.com/article/19/10/strace https://www.geeksforgeeks.org/strace-command-in-linux-with-examples/ ) which hooks all system calls and saves logs for functional analysis. Simple sandboxes just launch programs with "chroot()"+"strace()" for a few seconds, with all outputs sent for manual reviews; if more complex, has heuristics to guess what is important (in case of lots of submissions, so manual reviews have less to do.) Autonomous sandboxes (such as Virustotal's) use full outputs from all analyses, with calculus to guess if the app/SW is cool to us (thousands of rules such as "Should not alter files of other programs unless prompted to through OS dialogs", "Should not perform network access unless prompted to from you", "Should not perform actions leading to obfuscation which could hinder analysis", which, if violated, add to the executables "danger score" (which the analysis results page shows you.) CNS resources: Once the virus analysis tool has static+functional analysis, + sandbox, the next logical move is to do artificial CNS. Just as (if humans grew trillions of neurons plus thousands of layers of cortices) one of us could parse all databases of infections (plus samples of fresh apps/SW) to setup our synapses to parse hex dumps of apps/SW (to allow us to revert all infections to fresh apps/SW, or if the whole thing is an infection just block,) so too could artificial CNS (with trillions of artificial neurons) do this: For analysis, pass training inputs mapped to outputs (infection -> block, fresh apps/SW -> pass) to artificial CNS; To undo infections (to restore to fresh apps/SW,) inputs = samples of all (infections or fresh apps/SW,) outputs = EOF/null (if is infection that can not revert to fresh apps/SW,) or else outputs = fresh apps/SW; To setup synapses, must have access to huge sample databases (such as Virustotal has.) Github has lots of FLOSS (Open Source Softwares) simulators of CNS at https://github.com/topics/artificial-neural-network such as; "HSOM" (license is FLOSS) has simple Python artificial neural networks/maps which could run bots to do simple conversations (such as "ChatGPT 4.0" or "Claude-3 Opus",) but not close to complex enough to house human consciousness: https://github.com/CarsonScott/HSOM "apxr_run" (https://github.com/Rober-t/apxr_run/ , license is FLOSS) is almost complex enough to house human consciousness; "apxr_run" has various FLOSS neural network activation functions (absolute, average, standard deviation, sqrt, sin, tanh, log, sigmoid, cos), plus sensor functions (vector difference, quadratic, multiquadric, saturation [+D-zone], gaussian, cartesian/planar/polar distances): https://github.com/Rober-t/apxr_run/blob/master/src/lib/functions.erl Various FLOSS neuroplastic functions (self-modulation, Hebbian function, Oja's function): https://github.com/Rober-t/apxr_run/blob/master/src/lib/plasticity.erl Various FLOSS neural network input aggregator functions (dot products, product of differences, mult products): https://github.com/Rober-t/apxr_run/blob/master/src/agent_mgr/signal_aggregator.erl Various simulated-annealing functions for artificial neural networks (dynamic [+ random], active [+ random], current [+ random], all [+ random]): https://github.com/Rober-t/apxr_run/blob/master/src/lib/tuning_selection.erl Choices to evolve connections through Darwinian or Lamarkian formulas: https://github.com/Rober-t/apxr_run/blob/master/src/agent_mgr/neuron.erl Simple to convert Erlang functions to Java/C++ to reuse for fast programs; the syntax is close to Lisp's. Examples of howto setup APXR as artificial CNS; https://github.com/Rober-t/apxr_run/blob/master/src/examples/ Examples of howto setup HSOM as artificial CNS; https://github.com/CarsonScott/HSOM/tree/master/examples Simple to setup once you have access to databases.
-
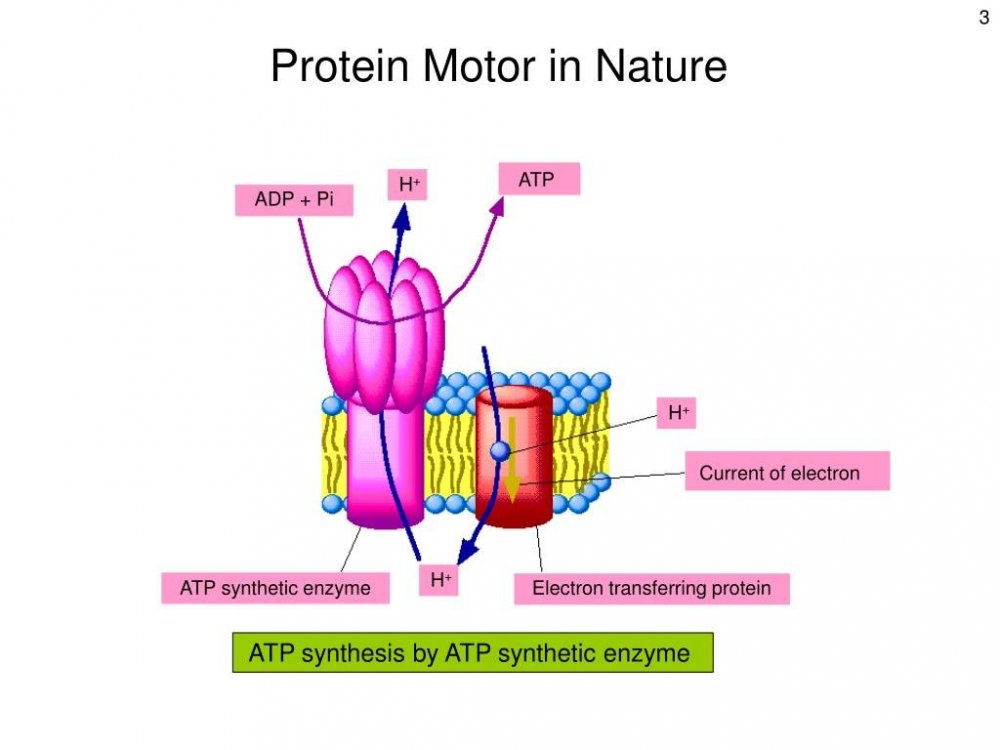
Wish to discuss how this could affect us, what lacks to adopt this, plus what more college/school sources exists about this. Had found previous articles about how humans use molecular motors based off of prootons, plus how cells of humans use protons for most tasks, but now can not locate this. Thought that, similar to humans, this uses fire/rust/redox. Thought had understood that inputs/outputs to/from proton-based power-sources would have electrons (or what the previous medium was; As inputs/outputs to power-sources, humans do not use electrons but use glucose/sucrose atoms for glucolysis) ) but that the internal structures of storage consist most of carbon/protons. Had found previous articles about robots that ran off of some sort of proton-based power-sources, but am now unable to locate this. The articles talked about how this was not done as central batteries but was distributed throughout the robot's chassis. Have any of you used/saw tools powered from protons? Would love to know more about this. Because renewables do not have constant output, would this do good to buffer the outputs for us, plus, versus lithium (which is not as abundant as carbon,) cost less for us?
-
Biological humans have lungs which use atmospheric gas to "fire"/"rust" our blood cells for synthases, which uses protons and allows human moves. This post allows all uses. https://futurism.com/proton-battery "What's A Proton Battery? Three Things You Need To Know." https://www.sciencedirect.com/science/article/abs/pii/S240582972300291X "Proton batteries shape the next energy storage" https://www.sciencedirect.com/science/article/abs/pii/S2405829722005220 "Accessing the proton storage in neutral buffer electrolytes using an electrodeposited molybdenum phosphate" https://www.azorobotics.com/Article.aspx?ArticleID=361 "The Best Sources of Renewable Energy to Power Humanoid Robots" https://onlinelibrary.wiley.com/doi/abs/10.1002/sstr.202000113 "The Renaissance of Proton Batteries" https://techxplore.com/news/2018-03-power-proton-battery-breakthrough.html "All power to the proton: Researchers make battery breakthrough" https://theconversation.com/how-protons-can-power-our-future-energy-needs-93124 " How protons can power our future energy needs" https://www.sciencedirect.com/science/article/abs/pii/S0360319918302714 "Technical feasibility of a proton battery with an activated carbon electrode" https://onlinelibrary.wiley.com/doi/abs/10.1002/sstr.202000113 "The Renaissance of Proton Batteries" Next is about human’s proton motors: https://www.sciencedirect.com/science/article/abs/pii/S0167779901015761 "Proton pumps: mechanism of action and applications" https://www.ncbi.nlm.nih.gov/pmc/articles/PMC10219236/ "Proton Pumps: Molecular Mechanisms, Inhibitors and Activators of Proton Pumping" https://www.cell.com/trends/biotechnology/abstract/S0167-7799(01)01576-1 "Proton pumps: mechanism of action and applications" Next is not specifics about protons as power sources, but is news about structures of protons: https://phys.org/news/2022-10-physicists-hitch-proton.html "Physicists confirm hitch in proton structure" This is a rough draft. A few days from now you should review this page for updates. Sources: https://swudususuwu.substack.com/p/biomimetic-robots-run-off-of-proton
-
Just as human's (billions of neurons plus hundreds of layers of cortices) CNS can parse old blueprints (plus watch other humans use those old blueprints to produce goods such as houses) -- to setup our synapses to parse new blueprints to figure out how to use tools to produce new goods -- so too could robot's (trillions of artificial neurons plus thousands of layers of cortices) artificial CNS do this. Just as humans can watch amateurs produce prototypes (plus parse blueprints later based off of those prototypes to mass produce goods) -- to setup the synapses of our CNS to allow us to produce new blueprints from new examples (to mass produce new goods) -- so too could an artificial CNS do this.
-
Oops, Clamscan is just a wrapper, for examples of FLOSS virus scanners, goto https://github.com/Cisco-Talos/clamav/ With regards to new CNS virus scanners: Just as (if humans grew trillions of neurons plus thousands of layers of cortices) one of us could pour through all databases of infections (plus samples of fresh programs) to setup our synapses to revert (from hex dumps) all infections to fresh programs, so too could artificial CNS with trillions of artificial neurons do this.
-
[quote="https://swudususuwu.substack.com/p/albatross-performs-lots-of-neural"]Possible to produce general purpose robos as autonomous tools, + close-to-human consciousness Kuka/Facteon/Fanuc can't work outdoors or as carpenters because Kuka/Facteon/Fanuc was just macros. Use DFS/BFS/IDDFS to run close to continuous functions as calculus General artificial intelligence allows autonomous robots to produce complex goods DFS/BFS/IDDFS pseudocodes/calculus: https://www.geeksforgeeks.org/iterative-deepening-searchids-iterative-deepening-depth-first-searchiddfs/ What problems to solve to have all goods (houses, vehicles, desktops, phones, foods) produced from autonomous robots for us? From Substack (CNS):
-
Yes. Have produced C and C++ implementations of all the major graph search algorithms (DFS/BFS/IDDFS/Simulated Annealing/BeamStack/A*/D*) and memorized most programming languages, and have lots of ideas on how to use map the continuous spaces of work robots to a series of graph nodes, with servo motions as edges. Have also absorbed thousands of pages of texts about artificial neural networks plus the human CNS, plus tons of FLOSS artificial neural network source codes, plus source codes for continuous feedback loops that control robots. All of these are suitable for robots with multiple arms to avoid self-collisions plus produce goods. Swarms of small robots are programmable as you would a huge robot with multiple arms to avoid self-collisions, so for jobs that require multiple human workers (not just to go fast, but because the nature of some jobs requires multiple human workers,) could do with just robots. Lots of FLOSS codes allow robots to merge inputs from multiple sensors to maneuver as good as humans can, some of these are based on artificial neural networks (based off of natural CNS,) some are just pure calculus. As far as know, the barrier to full robot work forces is just political; all of the movies of killer robots have most of us scared of robots, but as a solution you could just produce lots of small, soft robots just durable enough to withstand falls from scaffolds. Have poured over lots of texts of networks, could produce swarms of small robots that perform as slaves plus masters, where all the worker robots just use local CPUs to process raw data from sensors to produce small (low-bandwidth, compressed) maps of surroundings and broadcast those maps to the masters to plan paths for the robots, and the masters would just process those maps (plus goals) to produce outputs to broadcast to the worker robots. Could have one master, or for failover could have multiple masters, or could have robots broadcast to eachother (as peer-to-peer nodes, where each robot has full access to plans for goals,) or where an arbitrary robot is master (with advance setup of what robots to failover to as new masters.) The "democratic" solution of "all robots broadcast compressed data from sensors to all other robots and use local resources to plan their own paths/motions" uses more bandwidth and processor power, and has more issues such as synchronization errors, so is the least preferred of options, but could do this. Latest list of resources (and ideas) for autonomous robots (includes responses to replies from this plus lots of other forums): https://swudususuwu.substack.com/p/program-general-purpose-robots-autonomous Resources for artificial neurons/CNS: https://swudususuwu.substack.com/p/albatross-performs-lots-of-neural Examples of goals for robots: blueprint scans or AutoCad outputs, suchas houses. For graph searches; graph nodes = positions of pieces of wood, bricks or stones, edges = robot's motions. For artificial CNS; CNS training inputs = blueprint scans or AutoCad outputs, training outputs = data (from sensors) of humans that produce goods from those blueprint-scans/AutoCad-outputs, production uses for CNS; input scans to CNS, and CNS outputs motions for robots to produce those goods.
-
All that lacks are the structures of the sample databases. If you post Urls to such databases, could produce this in under 2 hours. This is not particular to ANN/CNS virus scanners but, rather, to all ANN/CNS problems; their sole limitation is CPU resources to crunch the databases, and access to huge databases. Examples of howto setup APXR as artificial CNS; https://github.com/Rober-t/apxr_run/blob/master/src/examples/ Examples of howto setup HSOM as artificial CNS; https://github.com/CarsonScott/HSOM/tree/master/examples Simple to setup once you have access to databases.
-
Was unfair to not include what the news says about vax, but can not alter original posts: If you trust the news, how long you are immune for varies across individuals, and the ingredients range from mRNAs (messenger RNAs, which cause your ribosomes to produce parts of viruses that allow for immune responses to future exposures to viruses,) to actual viruses (which also allow for future responses to viruses,) to pieces of viruses (which also allow for future responses to viruses.) Hybrids (and Teslas) use brake pads due to small generator resistances. Would gearboxes allow generators to turn much more fast than tires at stops (to maximize resistances, to recover almost all power,) and reduce use of gas? Could autonomous tools (such as Kukas/Fanucs) do this to reduce power uses? Teslas and hybrids use brake pads because the generator does not have enough resistances to perform stops. Gearboxes could have the generators turn more fast for stops, to increase resistances. This would not recover all power, so hybrids would use gas, but new pistons could use less gas: Fluid pistons are not fuelless but have lower noises plus use less gas.
-
For the scanners with heuristical analysis and sandboxes, the next logical move is to add artificial CNS. Not all scanners have such analysis and scanners, but clear that some such as Virustotal do, as the Urls show us. Earlier urls show Virustotal's heuristical analysis of Fdroid's package manager and review its behaviour through two sandboxes. A POSIX OS such as Linux has "chroot()" (run `man chroot` for instructions) so that the programs you test cannot alter stuff out of the test, and has "strace()" (run `man strace` for instructions, or look at https://opensource.com/article/19/10/strace https://www.geeksforgeeks.org/strace-command-in-linux-with-examples/ ) which hooks all system calls and saves logs, simple sandboxes just launch programs for a few seconds and dump such logs, with additional heuristics to guess which calls go to logs so reviewers have to look through less. Autonomous sandboxes use the ideas from first post, to flag programs that do system calls that would alter resources that are not part of the program under test. Heuristical analysis is similar to Clang/LLVM's static analysis tools (static analysis checks programs for accidental security threats such as bufferr over-runs/under-runs,) and you could use the FLOSS static analysis tools as a first basis for virus scanners, just add checks for deliberate security threats and flag those for manual reviews and warn not to run such programs before the reviews. https://github.com/llvm/llvm-project/blob/main/clang/lib/StaticAnalyzer is a FLOSS basis for analysis, has uses for virus scanners. As for the artificial neurons/CNS, those are as simple to use for this as the original post says. If you want, would not require too much effort to do this, but who has access to large sample databases for the artificial CNS?
-
To undo threatware/spyware/ransomware/malware for us, would you add artificial neural networks (artificial CNS) to virus scanners? Github has lots of FLOSS (Open Source Softwares) simulaters of CNS (at https://github.com/topics/artificial-neural-network , such as https://github.com/Rober-t/apxr_run/ ), which virus scanners could use to do this: Just have training data inputs = samples of infected files/programs, and outputs = original files/programs (or end-of-file for samples are just an infection and have no original files/programs to revert to), to produce artificial CNS to undo infections from files/programs Assume most antivirus programs have heuristical analysis and sandboxes, but if not here is how to do this: Search for open source (FLOSS) virus scanners (https://github.com/topics/virus-scanner has lots such as https://github.com/kylefarris/clamscan) and look at how those scan executables to figure out what programs do with your OS Most look for OS opcodes (such as “int” or “syscall”) or look at what libraries the programs load and search for instructions such as “jmp” or “call” that goto system libraries, to flag programs that alter other programs and flag programs that alter page flags to have W+X (lots of malware alters pages to have both writable and executable access, so virus scanners block such programs) To figure out what libraries a program loads, refer to the specifications of the OS’s executable format -- “Portable Executable” for Windows ( https://learn.microsoft.com/en-us/windows/win32/debug/pe-format https://wikipedia.org/wiki/Portable_Executable ), “Extended Linker Format” for most others such as UNIX and Linuxes ( https://wikipedia.org/wiki/Executable_and_Linkable_Format ) which would allow you to know what libraries a program loads at startup, plus those libraries’ functions’ addresses. Virus scanners should also look at dynamic loads of functions ( https://www.codeproject.com/Questions/338807/How-to-get-list-of-all-imported-functions-invoked ) such as from GetProcAddress, or just flag functions such as GetProcAddress For virus scanners to have better heuristical analysis, should flag programs that perform raw network accesses (versus OS functions to download/upload files), or that alter files of which the program is not the owner Some of this requires that you not just look at what functions the program calls, but also look at (if just constant parameters) or guess (if registers/addresses as parameters, antiviruses should use sandboxes or just flag all non-constant parameters to sensitive functions) what parameters the program passes to those functions Example outputs from Fdroid through sandbox/analysis: https://www.virustotal.com/gui/file/dc3bb88f6419ee7dde7d1547a41569aa03282fe00e0dc43ce035efd7c9d27d75 https://www.virustotal.com/ui/file_behaviours/dc3bb88f6419ee7dde7d1547a41569aa03282fe00e0dc43ce035efd7c9d27d75_VirusTotal R2DBox/html https://www.virustotal.com/ui/file_behaviours/dc3bb88f6419ee7dde7d1547a41569aa03282fe00e0dc43ce035efd7c9d27d75_Zenbox/html The false positive outputs (from Zenbox) show the purpose of manual reviews for programs that your sandbox flags
-
So far have not saw one autonomous robot do work for us What lacks for autonomous robots to produce for us? Over half of the population is dying from dehydration, starvation, or lack of houses Would produce the programs at no cost, just so the whole world doesn't keep going to hell but rather has some values Have searched but found no relevant results
-
Wanted to discuss how these chips could have uses to us. Have no affiliations to Elon Musk nor Tesla, and no financial stakes, just thought was cool if possible to use these chips to attach our CNS to virtual worlds. But doubt the chips have such uses, and would rather transplant CNS to robots. Want this physical form gone so won’t be forced to have E with everyone else from now on; am jealous of robots Want this meatbag gone once and for all. The problem is just, how to do so with small funds? If you had a million dollars, here is how to transplant your CNS to robots: Lookup maps of human CNS, produce a robot to replace all of your PNS (biological muscles and sensors) with mechanical servos/motors/actuators and sensors, program a medical robot to have your heart stop, remove your CNS from you, and transplant your CNS to the robot’s systems. You can rent medical robots, ( https://www.ncbi.nlm.nih.gov/pmc/articles/PMC3016020/ https://finmodelslab.com/blogs/operating-costs/medical-robotics-operating-costs ) but most of those just have 1 or 2 arms and would could not do much more than rip your cortex (and spinal cord) out of you. To remove, intact, all of your CNS and attach your CNS to the robot’s systems, would require complex robots that have thousands of small arms, such as one of the autonomous robot labs used to produce cars ( ), but small, to sever all of your nerves/axons plus attach your nerves/axons to a robot’s sensors/motors. If you have a million dollars, send a private message and I will do this for both of us Lots of cases of humans who have regrown severed nerves ( https://medicine.wustl.edu/news/regrowing-damaged-nerves-hinges-on-shutting-down-key-genes/ https://www.orlandohealth.com/content-hub/how-nerves-recover-after-trauma https://www.sciencedaily.com/releases/2010/09/100927141144.htm https://www.physicsforums.com/threads/check-out-bacterial-computers-pretty-cool-huh.73798/ ), so with a lab full of super complex medical robots, you could reattach your nerves/axons to digital circuits. You can lookup lots of cases of scientists that have hooked up bacteria ( https://www.ncbi.nlm.nih.gov/pmc/articles/PMC3971165/ https://pharmacy.ucsf.edu/news/2010/12/logic-gates-allow-bacteria-work-computers https://www.ncbi.nlm.nih.gov/pmc/articles/PMC2704931/ https://www.sciencedaily.com/releases/2022/11/221114111041.htm https://www.technologyreview.com/2021/11/09/1039107/e-coli-maze-solving-biocomputer/ ) or neural masses ( https://qz.com/computers-built-with-human-neurons-could-cut-emissions-1851010758 https://www.pcmag.com/news/this-lab-is-merging-human-brain-cells-with-computer-chips https://newatlas.com/computers/biological-artificial-neurons-connect-communicate/ https://www.nature.com/articles/d41586-023-03975-7 https://learningenglish.voanews.com/a/scientists-create-biocomputer-with-lab-grown-brain-tissue/7399612.html https://www.theregister.com/2023/03/02/organoid_intelligence/ https://www.npr.org/sections/health-shots/2022/10/14/1128875298/brain-cells-neurons-learn-video-game-pong https://www.technologyreview.com/2023/12/11/1084926/human-brain-cells-chip-organoid-speech-recognition/ ) to computers, so lots of progress you could use to transplant human's CNS into robot No affiliations to sources
-
"Brain-computer-interfaces"/"Neural interfaces" all fake with no uses to us? Looks as if Neuralink is just a euphemism for cybercrime and has no other purposes. More believable is electrodes that attach to neurons of animals, suchas: https://www.ncbi.nlm.nih.gov/pmc/articles/PMC3535686/ https://www.nature.com/articles/s41467-022-32775-2 https://www.nature.com/articles/s41565-024-01609-1 "Integration Theory of Consciousness* has thoughts of how to figure out if animals have consciousness. * https://bmcneurosci.biomedcentral.com/articles/10.1186/1471-2202-5-42
- 4 replies
-
-1
-
Simple, you produce a definition of "sexy thought" through calculus, and you measure the output of the neurons of the albatross, and look for CNS patterns that produce such thoughts. This is the general method to figure out the purpose an animal had a particular thought. Less general methods do not solve for all thought patterns, but do not require electrodes or other invasive tests: For sex, you could look at neuroscience as a whole to deduce that most animals have a CNS that releases sex hormones whenever the animal is around other compatible animals and has enough resources to reproduce, and that the purpose is because just an animal that evolves so exists. Such a small barrier, with your definition of consciousness all of the robots that handle purchases and deliver food to your houses already have consciousness. This simple food delivery robot does what you do, but is not conscious. This thread is more about the hard problem of consciousness, such as how qualia forms, how scientists conclude that information has mass, and that complex configurations of mass produce consciousness. Integration theory of consciousness is part of neuroscience that was produced to figure out how complex mass has to exist as to form qualias and true consciousness. But if you want to go for the smallest barrier, the greatest so-called "AIs" such as ChatGPT 4.0 obviously are not conscious, as they can not handle food purchases, whereas the artificial neural networks this thread describes would count as conscious, whether based on albatross or human CNS, as both would have the motor skills to walk to a store and perform purchases, and various forms of intelligences to figure out which food is good for us.
-
Simple, attach thousands of electrodes to an albatross's neurons. Show the albatross images (or another reproducible stimulus,) and look at responses of the albatross's neurons. From what have read of neuroscience, this is how lots of scientists* figure stuff out about an animal's CNS. * https://www.ncbi.nlm.nih.gov/pmc/articles/PMC3535686/ https://www.nature.com/articles/s41565-024-01609-1 How could you figure out if a human is conscious? Lots of anencephalic humans are born. Obvious: those are not consciouss. So how much CNS/functions must someone possess to count as conscious? From neuroscience: what quantizes this is "Integration Theory of Consciousness*" * https://bmcneurosci.biomedcentral.com/articles/10.1186/1471-2202-5-42
-
All the vaccine does is make you die, you should refuse thus. The solution is to remove pollution from us. Global warming causes trillions of dollars of physical damages, and traffic noise worsens spread of COVID (which causes trillions of dollars of healthcare costs,) how long for our leaders to realize the solutions for air traffic is: outlaw, and for land vehicles: subsidizes to switch to fuelless? Proof that traffic worsens spread of COVID, from our scientist leaders: https://www.ncbi.nlm.nih.gov/pmc/articles/PMC8499730/ Proof that COVID causes trillions of dollars of damages: https://healthpolicy.usc.edu/article/covid-19s-total-cost-to-the-economy-in-us-will-reach-14-trillion-by-end-of-2023-new-research/ Proof that global warming causes trillions of dollars of damages: https://climateanalytics.org/publications/carbon-majors-trillion-dollar-damages https://www.nature.com/articles/d41586-022-03573-z The cost of supercapacitors/ultracapacitors was the purpose that fuelless vehicles had huge prices. Solar offers abundant power sources for supercapaciters/ultracapaciters. Scientists now have methods to produce anodes/cathodes from trash (the rest of the capaciter is just carbun, the most abundant of natural resources): https://link.springer.com/chapter/10.1007/978-981-99-9931-6_16 https://www.sciencedirect.com/science/article/abs/pii/S0016236122039497 https://www.nature.com/articles/s41598-017-01319-w
- 5 replies
-
-6
-
You misunderstood; a lot of fake news touts chatbots (suchas ChatGPT 4.0) as "artificial general intelligences" although those do is parse everyone else's words to mimic language, and, of course, those do not have human consciousness. Those could not mimic human thoughts because all those have are text/words. Those are much more simple versus this. This would of course parse all available texts that exist as creative commons, but would also have physical forms with sensors (such as humans do,) and those physical sensors would allow true general artificial intelligences to move around true (or virtual) worlds, watch humans pickup tools, observe the tools' uses, or alone pickup tools and use at random to figure out how to put tools to uses. If you just want to go off what popular science says is the smartest bird, you would use a raven's CNS as basis for artificial general intelligences. Parrots are fawned over because parrots (as opposed other birds such as the albatross) have neural circuits that allow to mimic human speech, and most humans judge intelligence just based off of what how close animals or robots come to human speech, but robots that just performs human speech not have much uses other than as therapists. The albatross can perform cognitive tasks for months without rest stops: https://www.reuters.com/article/idUSL1N2MY2VO/ Most species with lots of intelligence are monogamous, and albatross is monogamous. Perhaps parrots would do too. Just as primates have vast differences as to tool use (chimpanzees just use stone tools, humans use computers,) perhaps birds have such vast differences. Regardless of whether you choose albatrosses or parrots, birds have evolved for longer than us, and do tool uses on par with chimpanzees with much less neurons, so for robots that must run all code local, should base off of avian CNS (as opposed to neuromorphic chips based off of human CNS,) to allow smaller chips plus lower power usages. Once scientists map the neural networks of albatrosses, simple to map the neural networks of parrots (or vice versa) for us. Once programmers produce parrot-CNS-based neural networks, simple to produce albatross-CNS-based neural networks (or vice versa) for us. Corvus corax does not have human speech but has the most tool uses.
-
Your post was "[Could you guess next thoughts just from access to past thoughts? And what if you had some of past thoughts wrong?]" and the implication was "How could artificial intelligences match human consciousness just from perfect analysis of human conversations, and what if some conversation was wrong?" and my response was that the former is not enough, but requires access to other data, and that with the other data, even with some errors, you could guess
-
Various simulated-annealing functions for artificial neural networks: https://github.com/Rober-t/apxr_run/blob/master/src/lib/tuning_selection.erl What sort of natural neural networks to base artificial neural networks off of for best performance, how various classes of natural neural networks differ performance-wise, how non-commercial (FLOSS) neural networks compare performance-wise, what languages are best for neural networks performance-wise, and how to put artificial neural networks to best use for us (although Tesla, Kuka, Fanuc and Fujitsu have produced simple macros for simple robots to mass-produce for us, lots of labor is still not finished as full-autonomous) Have read tens (hundreds?) of thousands of pages about neuroscience and artificial neural networks. CPUs can use less than a second to count to 2^32, and can do all computations humans can with just 2 numbers. From some neuroscientists: humans (plus other animals) use quantum algorithms for natural neural networks. The closest to this computers do is Grover's Algorithm (https://wikipedia.org/wiki/Grover's_algorithm) As artificial quantum computers continue to cost less and less (Microsoft Azure allows free cloud access to quantum compute,) this should allow more fast artificial neural networks. As opposed to lab-robots that run simple macros, how to produce robots small/soft enough that humans would not fear robots that work outdoors to prouce for us, and with enough intelligence to watch humans plant crops or produce houses and figure out how to use swarm intelligences to plant crops/produce houses for us full-autonomous?


.jpg.47a23def5a92614cfb9228fbaebc1a88.jpg)