shivajikobardan
Senior Members-
Posts
56 -
Joined
-
Last visited
Recent Profile Visitors
The recent visitors block is disabled and is not being shown to other users.
shivajikobardan's Achievements

Meson (3/13)
0
Reputation
-
shivajikobardan started following Authentication in Pretty Good Privacy Confusions , Is there some restrictions on values of p,q,d,e etc in RSA algorithm while trying to encrypt English Ciphertext? , What's the technique used by this teacher to solve ax+by=GCD(a,b) in RSA Algorithm-Cryptography? and 7 others
-
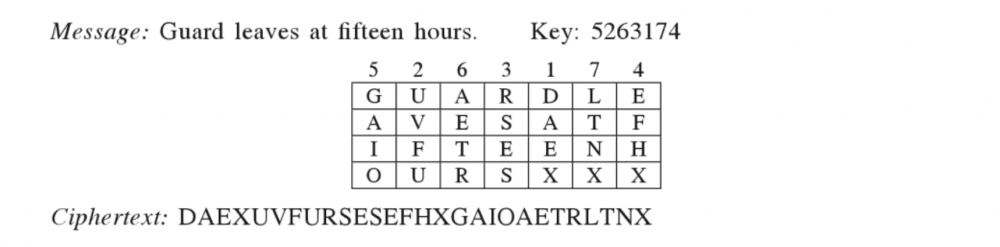
I'll present few cases of RSA encryption: [math]CT=(PT)^e mod \, n[/math] [math]PT=(CT)^d mod \, n[/math] CT= Cipher Text PT=Plain Text e*d/m should give remainder 1, where; m=(p-1)*(q-1); where p, q are 2 prime numbers. A) Sender takes p=3, q=11. The value of e=3, d=7 satisfied the remainder=1 condition. So, if sender wants to send "SELL": S=19, CT=28 E=5. CT=26 L=12, CT=12 L=12, CT=12(? What to do to not get the cipher text same as plain text without making things too complex and still being able to do it in paper manually?) B) p=2, q=11 e=3,d=7 I'll only write CT here(i.e S=17 means that 17 is a cipher text for S after RSA encryption): S=17 E=15 L=12 L=12 (Same here? why? Because of d,e being the same?) C) p=13, q=11 d=13, e=37 So, S=95 E=93 L=12 L=12 (Again got the same value, what is this? Even with different values of p,q,d,e!) Questions: a) Is there any restrictions if among p or q, anyone should be greater? b) Is there any restrictions like which of the d or e should be greater? I know e<m and e>1 And e should be relatively prime to m, i.e GCD(e,m)=1. GCD(13,120)=1 For d, de mod m=1 c) Would there be any cases, where while decryption, we would not be able to get the plain text due to some reasons (like if not choosing values properly for d,e,p,q in english alphabet encryption? This is the main confusion that is making me ask this )
-
https://www.youtube.com/watch?v=di3OXhHMZmI It starts at 6:16 It's the part where he's pointing his hand in this picture. I didn't get it although it's pretty mechanical, so I'd like to learn that technique as this is really useful in RSA algorithm(rather than having to memorize some values). I've been searching for a method like that since I saw this problem(been months) but could not find a technique like that. And it was always about just do it rather having any mechanical method like this one. So, I want to learn this. Or, if you have any other simple methods to solve this equation, please tell me
-
This is taken from this book: https://books.google.com.np/books?id=k-rKDwAAQBAJ&pg=PA91&dq=advanced+encryption+standard&hl=en&sa=X&ved=2ahUKEwj_nIeU6t75AhUMGKYKHbJWDms4oAEQ6AF6BAgGEAI#v=onepage&q=advanced%20encryption%20standard&f=false Page 102 I've used this method given in this pdf below to calculate "mix column" step output. https://www.networkdls.com//Articles/AESbyExample.pdf It's in page number 9. I'm trying to find this below ( + means XOR here) 1*36+2*b9+3*a5+3*38 =36+69+f4+48 =e3
-
First I'll give some context about how the book's written as many books are presenting it in different ways. Reference: CRYPTOGRAPHY AND INFORMATION SECURITY, THIRD EDITION By PACHGHARE, V. K. Confusions: 1) Why is Expansion Permutation called so? The name sounds very contrary to what what you'd expect a Expansion Permutation to do. You'd expect it to work like say 4:16 decoder. 2) Why is Expansion Permutation done here? The number of bits remained the same. What's the difference? Or are we calling after discarding parity bits as "Expansion Permutation"? 3) Plus I'm reading some answers here and there. And I'm hearing that the information that I presented here is wrong. 4) One comment I saw in some other post is that, "(IP) and and (EP) are applied to the plaintext, not the key" https://en.wikipedia.org/wiki/Data_Encryption_Standard According to it, Wikipedia vs my first source: a) No initial permutation is done on key. b) No expansion permutation is done c) Only left shift happens, no right shift as shown in my first figure. There're some other sources which seem to be taken from wikipedia and sound similar to it. They're given follows. Others: 1) https://www.lri.fr/~fmartignon/documenti/systemesecurite/4-DES.pdf Go to page 19. So, which one should I believe? I think WikiPedia should be believed as many are copying from it, but I'm not sure. Which version is correct according to the actual DES? 2) Source: https://academic.csuohio.edu/yuc/security/Chapter_06_Data_Encription_Standard.pdf
-
An example of how probabilities are calculated in poker hand. Probability and Statistics with Applications: A Problem Solving Text By Leonard Asimow, Ph.D., ASA, Mark Maxwell, Ph.D., ASA You can ask me for more details about question, I won't paste them here, as it'd make the question too lengthy to view. What problem I'm trying to do? I am trying to find expected probability for random number independence testing aka poker test. We've 10,000 random numbers of five digit each. They're assumed to be independent. My calculations-: 1) Full house 10C1*9C1/10,000 =0.009 I'm correct. My only confusion here would be the denominator. Why is it 10,000? According to the above example, should not it be 10C5? Explanation of my thought process-: First pick 1 digit out of 10 digits. Then next, pick another digit(only 1 digit as we need a pair), out of remaining 9 digits. 2) 1 pair: Again I looked at that highlighted figure. For one pair, from 10 digits, choose 1 digit. That 1 digit makes a pair. Now you've remaining 3 choices. But none of those choices can be same to each other. So, 10C1*9C1*8C1*7C1/10,000 =0.504 I'm correct here as well. 3) 3 of a kind: Here, I need to pick only single digit for 3 places, then 2 different digits for the remaining 2 places. So, 10C1*9C1*8C1/10,000 =0.072 Here, also I'm correct. But not anymore. 4) Four of a kind: So from 10 digits, I need to pick 1 digit and out remaining 9 digits, I need to pick another 1 digit. So, it should be 10C1*9C1/10,000 But it becomes similar to full house. This is wrong. I don't get why this became wrong. 5) 5 different digits: This should've been simple, I got the answer but I got the answer greater than 1. 10C1*9C1*8C1*7C1*6C1/10,000 =3.024 I'm not sure why I got this. I am skeptical about the denominator since the start as I feel that's randomly chosen here unlike above where we did 52C5. If I increase 1 "zero" in denominator, the answer would be correct. (I've seen techniques like 10/10*9*10*8/10*7/10*6/10, but i prefer to do it as per the first poker example figure I showed so that it becomes simple for understanding). 6) Five of a kind: It should be 10C1/10,000 =0.001 but it is instead 0.0001, so it's asking for another "zero" in the denominator for correct answer. I don't know why. We have just 10,000 random numbers. This is the reason for studying this-: https://genuinenotes.com/wp-content/uploads/2020/03/Random-Numbers.pdf
-
These are the steps of indexing in Lucene given in our syllabus-: I understand the second step clearly. But I don't understand the first and third step. It's not mentioned clearly in this figure imo. Can you clear my confusion? Plus the sources that I refer don't even mention it like this, they explain it differently. I'm not sure from where this is copied from. What are we doing in first vs third step as written in that figure text? Why was indexwriter created first and not used later? Because according to my information that I've collected, you can also use indexwriter to add/remove/update indexes. I've a good feeling that all of this information is incorrect but this is what's written in my teacher's notes so I'm not 100% sure of it. And even if it's wrong, they'd expect us to write the same thing in exam, so I've to learn it.
-
Design the markov model and transition matrix for the given data. Answer the following questions based on the mode. a) If a person purchase coke now the probability of purchase of coke next time is 80%. b) If a person purchases pepsi now the probability of purchasing pepsi next time is 70%. Then, Find the probability of using coke for a current pepsi user in 4th purchases-: My solution-: This is the transition diagram. This is the transition probability matrix-: So, what I did was basically to Took this TPM(Transition Probability Matrix) to the power 4. My basis for doing this was this source-: https://www.math.pku.edu.cn/teachers/xirb/Courses/biostatistics/Biostatistics2016/Lecture4.pdf So what I got was-: Now I am assuming that the rows means FROM and column side means TO. And the first element of row and column is "Coke". So, to find from Pepsi to Coke, I'd go to second row and first column, the value would be 0.5625 But the problem is that, I've conflicting source which claims the answer is sth else-: It solves it like this-: P=TPM p=Current distribution=[0 1] Now, for 2nd purchase p²=p*P=[0.3 0.7] For 3rd purchase-: p³=p² * P =[0.45 0.55] For 4th purchase-: =[0.525 0.475] Thus, it concludes that the required answer is 0.525. Which one is correct in your opinion? Plus admins, please fix this issue. I'm not getting reply notifications once I ask and receive an answer.
-
I am studying about components of a system. Activity-: It is What entities do to cause changes is activity. It is represented by time period of a specified length. Event-: Event is defined as an instantaneous occurrence that might change state of the system. Endogenous events occurs within the system and exogenous events occurs outside the system. eg-: making a deposit is an activity, arrival of customer is an exogenous event and completion of service of a customer is an endogenous event. I don't see any difference between them. making deposits can also be an event as it'll change the state of the system. i.e money in bank account. The one difference that can be taken from these definitions is "instantaneous" vs "time period' but the examples don't deliver anything about it. Below is the figure from a slide available online.
-
We want authentication ie -> the source written in the received message should be the actual real source that sent the message. ->information should not be altered in the way (data integrity) So to support this, book does this. But I can’t realize how it is helping authentication? How do we know the source in the received message is actual source? (You might say by comparing the received hash and computed hash of received email message) but that I can’t feel it how. Leaving PGP aside, What is the best way in real life to know that the message is sent to me by someone whom I know? Maybe if we have some well established secret code between us. authentication means-: 1) when information is received from a source, authentication means that source is indeed as alleged in the information. 2) information was not altered along the way. this authentication is also referred to as maintaining data integrity. RSA at sender-: with sender's private key My genuine questions(I am aware about symmetric and assymetric encryption-here the text explicity said public key for encryption and private key for decryption. Any scientific reason behind that) { Why not use sender's public key here? Why not use receiver's private key here? Why not use receiver's public key here? } RSA at receiver-: with sender's public key. { Why not use sender's private key here? Why not use receiver's private key here? Why not use receiver's public key here? }
-
Definition 1-: Taken from here-: https://research.cs.queensu.ca/home/cisc462/moni/m3.pdf This in my opinion, just makes things complicated. Decision problem is just something where we get output in the form of yes/no…T/F…etc. But it says it gives input true or false…can you give me example about that? I thought the goal of decision algorithm should be to find answer in the form of yes or no. Definition 2-: Source-: http://www.cs.virginia.edu/~evans/cs302/classes/class17.pdf This says something else. Definition 3-: Source-: https://www.youtube.com/watch?v=WdWbi5-OIy8 This says something else. I am confused in this seemingly simple thing. What I feel is that “if there is an algorithm to solve it(basically a turing machine) then it is decidable”...else undecidable. Am I right?
-
How can same machine take same machine as input(is it same machine taking encoding of itself as input—if that’s the case, what does that means some examples to understand this)? (in Universal Turing Machine, i know it was possible). What does that even mean here? I feel like adding a turing machine flipper is like cheating and should not be allowed as well.
-
R=(01+010)* For it I made the below nfa which i believe seems correct. Plus the tutorials that I am following also make sure it’s correct. Q0 is initial state(forgot to mention in figure). R=(01)*+(010)* But idk how to convert this to NFA What will be languages accepted by this NFA? Won’t it be the same as the above one? (for some different question) I got small hint about this. It was to add epsilon transition, but I don’t understand the need for it. Source-: https://www.cs.wcupa.edu/rkline/fcs/nfas.html