-
Posts
1903 -
Joined
-
Last visited
Content Type
Profiles
Forums
Events
Posts posted by fiveworlds
-
-
You can build a Linux distribution easily enough and then make a custom Desktop for it.
0 -
Quote
I was born very poor. A family of survivors from the Second World War purge, not a Jew, nor a Kossac, not a Gipsy but part of them, só, no sides to shelter my grand parents. I was borm very poor and remeber starving.
Okay this went weird fast. Look this is the code I have. It is more of a proof of concept than anything at the moment and is way messier than I would like since I don't really have time to look at it after work. As I said instead of a DPLL algorithm which randomly assigns values to literals and can take exponential time. I create a custom hashmap that works like a template and as a result can run in n^2 time or less while still getting a correct result.
0 -
Quote
But you can see the http? If it's without the s, do not connect with a login and password, because it means that your connection is not secure. In this case you must reset your OS (windows or mac) But you should at least see the padlock on the web browser.
It is unlikely the problem is because of HTTPS.
QuoteFacebook and youtube is especially bad for it
Facebook and youtube have lots of content so it is harder for your computer to load them which suggests a CPU or GPU problem possibly causing a short circuit somewhere. A short circuit could possibly be caused by moisture but could also be a manufacturer fault. I would recommend the following:
- Check to see if you got a driver update recently and if so then downgrade the driver to the ones provided by your manufacturer.
- Open your computer and check that there is no corrosion/dust/moisture in your machine. (Note if you have a warranty on your machine you may prefer to just return it to the manufacturer)
- Reinstall your operating system to ensure you don't have any malware.
If the computer is very old it may be worth replacing it at this point but if it was bought recently you can.
- Return the computer to the manufacturer for repair.
- Take it to a competent professional who does PCB repair. Note the vast majority of computer repair shops don't have the equipment for PCB repair.
0 -
-
Quote
I was thinking about using WebRTC though but I was confused as to what would be the best.
I did that for my FYP https://github.com/davidmather/fourthYearProjectImplementation
It is supposed to be a multilingual videocalling service e.g. I talk to you in English and you hear French, German etc. and you should be able to specify commands to the other end of the call by talking like show me the kitchen for a call linked to your house. I have code in the frontend javascript for a download which sends a file to the person on the other end of the call via WebRTC. That should be what you are looking for?
1 -
Quote
I think this one does not accept aa and bb but its not correct because it does not accept any string.
You are correct. You could modify it to have a final state somewhere that transitions on some other letter like c?
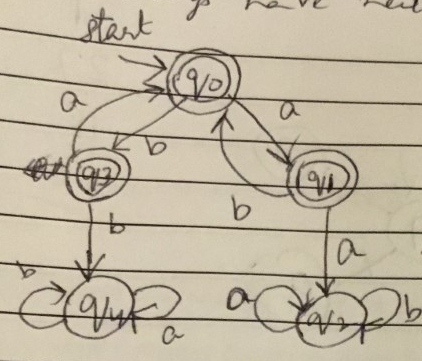
A DFA must end on a final state e.g. the 2 circles.
Starting from q3 you can accept aa as it will transition to q0 then q1.
Starting from q1 you can accept bb as it will transition to q0 them q3.
QuoteI want to create a DFA which does not accept aa and bb as substrings.
You can read more than one letter at a time and make all final states lead to an exit state if it reads them. You can use anything that fits in combinatorial logic including don't care terms to read a regex e.g. BxBxxxB.
***** Challenge Question *****
A DFA is a part of a Turing machine. Show that a 3 head Turing Machine can accept the regex B*B*B without changing state by creating a table of moves. Hint. You may stop moving a read head if you read a letter.
1 -
I saw that and ordered an adapter in the hope that it works.
1 -
I have a HDTV for a few years but now my tv box isn't working and I get an error about not having HDCP? Does anyone know about this?
0 -
I am joking, I cannot afford to go to college because my family is poor. I also work long hours most days so I don't have time to write an academic paper. But I have read basically everybody else's notes on P vs NP.
Look at the table I provided again what happens if I replace A-F with the numbers 0-6? For P vs NP we are asked to create a Turing machine with a deterministic finite automaton. A DFA just maps symbols to other symbols. Once we have the table from before everything else is just how to we convert the input into the format of the table which is basic maths.
Say I give you the clause 123, 167, 253 I need that in the form 0-6 so what do I take away to get it into that format? The exact number provided right?
Now when I match that against another clause say 145,169,267 well then I do basic subtraction (145-123=22, 169-167=2, 253-267=-14). We can easily see that 22 is not between 0 and 6 so the clause has no bearing on the satisfiability of the initial clause.
If the number after subtraction is between 0 - 6 then we follow the table and transition to a state where we save the answer to the 8 bit memory and check if it is unsatisfiable. The for loop is basically instructions about how to move the Turing Machine's read head. In my case I am using 2 read heads.
An actual proof of P vs NP would have all the necessary transition tables and circuit diagrams to make that work. Simply having a working java class isn't sufficient.
0 -
Quote
In 21st century Western countries almost all of us have had decent nutrition and ample opportunities to acquire knowledge and cultivate our minds, and therefore most of the variation in how smart we are relative to each other is determined by our innate design which we had no control over.
That simply isn't true. Some kids have parents that don't give a damn, they drink or have problems with drugs or money. Some schools have outdated textbooks, broken laptops and no or limited access to the internet.
https://www.nytimes.com/2018/04/16/reader-center/us-public-schools-conditions.html
Some students don't have the internet at home or have very bad internet and only reference books.
Some families need help at home and take kids out of school to help out on the family farm or are forced to help out on the farm after school. https://www.dailymail.co.uk/news/article-6728209/Children-skipping-education-help-family-farm-drought.html
Some kids don't have access to extra curricular activities like sports or music. https://www.theatlantic.com/education/archive/2015/01/the-activity-gap/384961/
Some kids don't have access to tools and equipment required to study certain activities. One example could be a student in my school built a wooden boat as a school project from wood and tools his family had just lying around and got an A1 in the woodworking class. I had little to no tools at home and barely got a C.

But it gets worse. Some kids have access to tools like Unreal Engine because their parents can easily afford computers capable of running. For a long time I didn't have a computer that could run unreal engine at all.
Then there is the university places gimmick. Access to university is controlled by a points system. The number of places puts people in their boxes. Poor people do the low paid courses and rich people do the better courses. There is some allowed movement between rich and poor but really the government doesn't want too much change. If poor people start to do better then the points increase. https://www.theguardian.com/education/2020/aug/13/almost-40-of-english-students-have-a-level-results-downgraded
3 -
Hmm I would like to use my answer for my phd thesis. I suppose there isn't much harm in telling.
A
B
C
D
E
F
AC
AD
AE
AF
BC
BD
BE
BF
CE
CF
DE
DF
ACE
ACF
ADE
ADF
BCE,
BCF
BDE
BDF
0
F
T
F
T
F
T
F
T
F
T
T
T
T
T
F
T
T
T
F
T
T
T
T
T
T
T
1
F
T
F
T
T
F
F
T
T
F
T
T
T
T
T
F
T
T
T
F
T
T
T
T
T
T
2
F
T
T
F
F
T
T
F
F
T
T
T
T
T
T
T
F
T
T
T
F
T
T
T
T
T
3
F
T
T
F
T
F
T
F
T
F
T
T
T
T
T
T
T
F
T
T
T
F
T
T
T
T
4
T
F
F
T
F
T
T
T
T
T
F
T
F
T
F
T
T
T
T
T
T
T
F
T
T
T
5
T
F
F
T
T
F
T
T
T
T
F
T
T
F
T
F
T
T
T
T
T
T
T
F
T
T
6
T
F
T
F
F
T
T
T
T
T
T
F
F
T
T
T
F
T
T
T
T
T
T
T
F
T
7
T
F
T
F
T
F
T
T
T
T
T
F
T
F
T
T
T
F
T
T
T
T
T
T
T
F
See the table this is all the possible things that could be wrong in 3 Sat. I wrote a generator to create the above table. e.g. Solver solver = new Solver. I assign it to a static custom HashMap() which has a get method where I pass clause a and clause b. It then checks the hashmap for the False values.
It is easy to see that what it returns is a boolean array with 8 terms. e.g. for A it is FFFFTTTT and so on.
The generator is only used in the constructor so it has no effect on the runtime in the worst case.
We call the solver with an array of clauses and then iterate over it like so.
boolean[] satisfiable = (TTTTTTTT) for (int i =0; i <array.length; i++){ for(int j=1; j<array.length; j++){ //get value from the hashmap //join to the array //eg. a=FFFFTTTT } //check if satisfiable is FALSE // return // else reset the value satisfiable = (TTTTTTTT) }It is easy to see that this is O(n^2) in the worst case. It is similar enough to bubblesort that it could be even faster.
I can easily extend the array to K-Sat by increasing the size of the Custom HashMap generator. To generate the table from above I pass in
String[] array = {"a","b","c","d","e","f"}; char[] charArray = {'a','b','c','d','e','f'};So I can extend it by adding g,h,i,j,k etc.
0 -
Quote
Do you have the skil for it? y background is Math but it is not a cumbersome paper.
Give me, please, a more adult answer,
I can obviously read your paper and it is wrong. You asked for a hint and I gave you one. Here's another you can solve it in O(n^2) or less with parallelization. I feel it would be better to write it as an academic paper with references. But I am awful at writing papers and let's face it "Give me, a more adult answer" will be exactly the kind of annoyance I can expect if I publish. There are people with phds who haven't solved it for years I doubt they will look favourably on somebody who doesn't have one (There is quora questions on this exact thing)
-1 -
I already have a polynomial time algorithm for k-Sat in Java . I don't have a phd and can't publish it in a formal journal as a result. So what is in it for me to help you? I'm sure nobody will solve it until I am in a position to publish anyway.
Your proof is wrong by the way.
-2 -
The python documentation uses the word dictionary to describe variables ithat are key-value pairs.
The dictionary is defined here.
d={'col1': [1, 2], 'col2':[3, 4]}
1 -
It isn't perpetual motion as it requires energy from input sewage. Extracting useful products such as energy from sewage isn't a new idea either. Strange was right to close the thread.
0 -
Quote
Can anybody please help?
I usually watch Udemy/YouTube videos. There is a general rule of thumb to do well (in college)
- Invest in a fast computer and internet connection. It should have be able to boot Windows, Mac, and Linux at least (3TB hard drive)
- Comment every function. Try to follow standards like JavaDoc.
- Use design patterns. (download cheatsheets)
- Use private variables with getters/setters everywhere.
- StackOverflow is your friend. When asked to code a function it will generally be one the lecturer copied from a website somewhere.
- Use a good IDE, some examples are Intellij idea.
This guy makes a joke about it but it "should" get a good mark.
0 -
Quote
Now that he is immune he shouldn’t have to worry about the mask
A test is necessary to determine if the person is immune.There is no reason to assume that he has immunity after getting the virus once.
Medicine likes to put prefixes on things. "A" in front of a word means logical negation of the following word so "Asymptomatic" means not symptomatic. The person is sick but a third party would never be able to tell they were sick by looking at them. They may also think that they aren't sick or that their symptoms are normal.
Take an imaginary person Jim. He has hayfever and is always sneezing. He acquires the coronavirus infection and sneezes but thinks nothing of it because it is normal for him to be sneezing in the summer. Other people living with Jim know he has hayfever and think nothing of his sneezing.
0 -
-
Quote
What is the purpose of the key stream?
Historically there was the idea of the enigma machine. This allowed you to make simple string replacements using a particular setting or key. If you had the key then you could decrypt the message encrypted by enigma. This was a bit insecure, at the time character -> character mappings worked relatively well eg A = C, D=K and so on as computers became more powerful they could easily decrypt such messages therefore a more powerful method of encryption was required.
The new method involved using complex maths/pseudo-random number generators to create a set of replacements based on a key which was called the keystream. Instead of single character -> character replacements it instead made replacements based on an array index (determined by some algorithm) in the set of replacements so given the keystream { A, F, G, I, K } . The first letter in the message would undergo some operation with the some letter in the keystream and so on until you have an encrypted message. So if you and I had the key and the generator we could send encrypted messages to each other. This was still insecure, if for instance you were attacked by an enemy they could send encrypted messages pretending to be me. Modern generators will use the idea of a public and private key. The public key can generate the keystream to decrypt messages. The private key can generate the keystream to encrypt messages.
One thing to note is that the keysteam + generator/function must always create 1-1 mappings between characters for encryption e.g. A->G, B -> D. If you have anything greater than 1-1 mappings e.g. AK -> G and BG->G you have what is known as a hash which isn't easily reversible. Hashing is usually used for passwords to ensure that a hacker cannot get access to login information if they manage to hack a database somehow.
0 -
The error is caused by an outdated Truffle and inconsistent Solidity version not returning the expected JSON result to putBalance. The tests themselves are not written in JavaScript. You are better off learning the latest versions of Truffle and Solidity .
$ sudo apt-get update $ sudo apt-get install nodejs $ sudo apt-get install ethereum $ sudo apt-get install geth $ sudo npm install -g truffle $ mkdir MetaCoin $ cd MetaCoin $ truffle unbox metacoin //Open a seperate terminal and run $ cd MetaCoin $ testrpc //Back in the original terminal $ truffle test
 1
1 -
-
Quote
I am seeing a tutorial, it shows me the interfaces which I have on my computer but wireshark is showing me different interfaces.
I am assuming it is the tutorial to ping google and get the interfaces shown, you didn't apply the filter for google. It is highly unlikely to be the same as what is in the tutorial but you look to be doing the correct thing.
1 -
Quote
Yeah, it's tough because I have no idea how to formulate a conversation on the topic.
I assume you aren't making the final decision so don't take that responsibility. You should create a PowerPoint presentation referencing the various options that are available and present that to the other members of your team so an informed decision can be made. If you are uncomfortable doing so yourself I'm sure you can recruit a consultant on a temporary basis to do so.
2 -
A drone for footing turf.
0








What separates the P vs NP problem from a general labourer asking "can we solve the hard stuff as quickly as the easy stuff"?
in Computer Science
Posted · Edited by fiveworlds
Yeah that is basically it. Two American academics came up with some new idea for his phd and then has to defend it. What is so special about these non-deterministic machines when my normal computer does everything I want? The question is there precisely because he didn't have a proper answer to that and nobody else seems to either even after offering a million dollars it. Heck he even went so far as to say if we prove the wrong thing we break banking security. Which is ridiculous really even if one or two encryption algorithms such as RSA won't work anymore there are other ways banks use to secure your data such as passwords and multi-factor authentication.
It doesn't actually say that. There are plenty of hard problems that simply aren't in NP computing a factorial being an example. We are always looking for ways to make computers faster, more ram, better CPU etc. Why? because it is worth big money, forget about the fact that it is a stupid question and think about what better algorithms mean for people. Some guy comes up with a faster algorithm for drawing light to a screen and now we have new graphics cards that are worth billions to the companies that develop them advertising "ray tracing".
Lots of computing stuff is just opposite to how we actually think. The guys who have a vested interest in wanting P!=NP say it isn't and the guys who don't care either way such as Donald Knuth say P=NP. Bear in mind Donald Knuth literally wrote the book on computer programming.